External Threats
What are External Threats?
External Threats are those threats that refer to any potential danger, risk, or malicious activity that originates from outside the organization and has the potential to compromise the confidentiality, integrity, and availability of its sensitive information, systems, or operations. External entities, such as hackers, cybercriminals, competitors, or other malicious actors, typically pose these threats and seek to exploit vulnerabilities in an organization’s cybersecurity defenses.
Types of External Threats
Understanding these threats is pivotal for organizations aiming to fortify their defenses and protect against the ever-evolving challenges in the enterprise security landscape. Let’s delve deeper into the various types of outside threats that organizations commonly face in enterprise security:
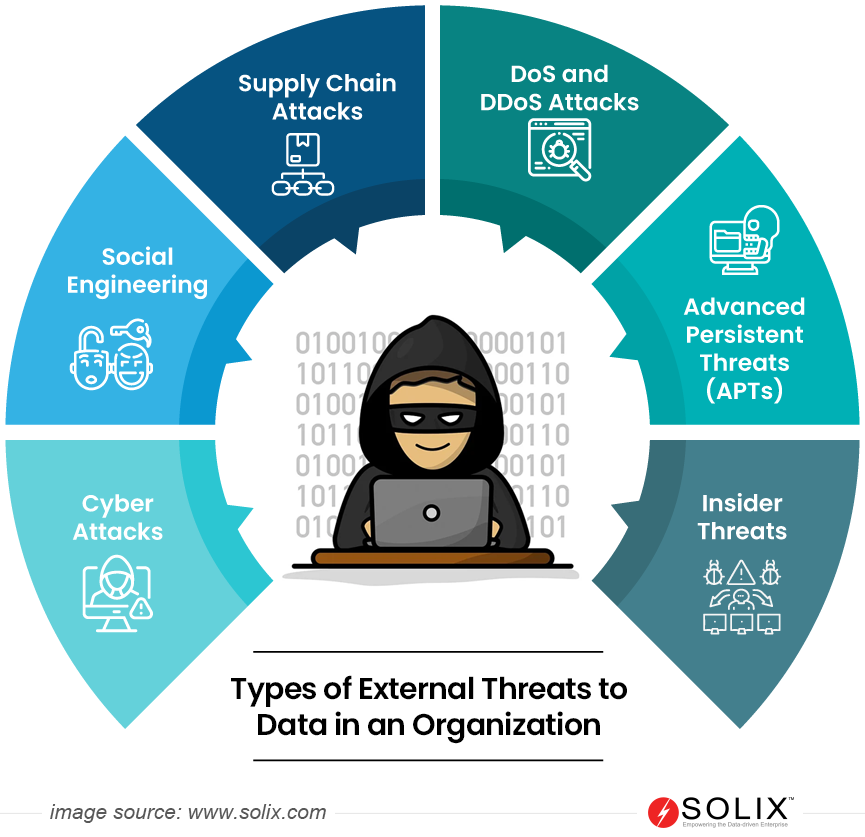
Different types of External Threats
- Cyber Attacks: Cyber attacks encompass a wide range of malicious activities intending to compromise the security and functionality of an organization’s digital infrastructure. This category includes:
- Ransomware Attacks: Malicious software is designed to encrypt a victim’s files, demanding a ransom for their release.
- Phishing Attacks: Deceptive attempts to trick individuals into divulging sensitive information, often through fraudulent emails or websites.
- Malware Attacks: Deployment of malicious software to disrupt operations, steal data, or gain unauthorized access.
- Social Engineering: Social engineering involves manipulating individuals within an organization to divulge confidential information or perform actions that could compromise data security. This can include tactics such as pretexting, impersonation, or manipulating employees into providing sensitive information.
- Supply Chain Attacks: External Threats can exploit vulnerabilities within an organization’s supply chain. This involves targeting third-party vendors, partners, or suppliers to gain access to the organization’s systems or compromise the integrity of the supply chain.
- DoS and DDoS Attacks: Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks aim to disrupt the availability of services by overwhelming a system, network, or website with a flood of traffic. This can lead to downtime, impacting business operations and causing financial losses.
- Advanced Persistent Threats (APTs): Advanced Persistent Threats (APTs) involve extended, targeted cyber assaults, enabling adversaries to access networks without detection. These threats are often highly sophisticated and may be state-sponsored or carried out by well-funded cybercriminal organizations.
- Insider Threats: While often considered insider, internal threats can also have external origins. These threats involve individuals with authorized access to an organization’s systems and data who intentionally or unintentionally pose a risk by disclosing or misusing sensitive information.
In conclusion, External Threats pose significant risks to data security, potentially compromising sensitive information. However, organizations can mitigate these risks by strategically implementing robust data security tools like data masking, access control, etc. By obscuring sensitive data, they create a formidable barrier against unauthorized access, ensuring the integrity and confidentiality of their valuable information.
FAQ:
What are typical examples of External Threats?
External Threats encompass malicious activities from outside an organization, such as cyberattacks by hackers, phishing attempts, or malware infiltration targeting systems, networks, or sensitive data.
Are there industry-specific External Threats that organizations should be aware of?
Yes, industries such as finance, healthcare, or energy may face specific External Threats tailored to exploit sector-specific vulnerabilities or target valuable assets, highlighting the importance of industry-specific threat assessments and cybersecurity measures.
Can emerging technologies introduce new forms of External Threats?
Yes, emerging technologies like AI, IoT, or blockchain present new attack surfaces and vulnerabilities that adversaries may exploit to launch sophisticated cyberattacks or manipulate data. This underscores the need for proactive risk assessment and security measures to address evolving External Threats.
How does the dark web contribute to External Threats?
The dark web serves as a marketplace for cybercriminal activities, offering illicit goods, services, and stolen data. It provides adversaries a platform to collaborate, exchange tools, and orchestrate cyberattacks, posing significant External Threats to organizations’ cybersecurity defenses.





